Members and Collaborators
- Rajat Tandon
- Pithayuth Charnsethikul
- Jelena Mirkovic
- Dhiraj Murthy, UT Austin
- Ishank Arora, UT Austin
Publication : Privacy Enhancing Technologies Symposium 2022
Accepted Artifact at PETS 2022: Link
Keywords list for sensitive content: Link
Overview
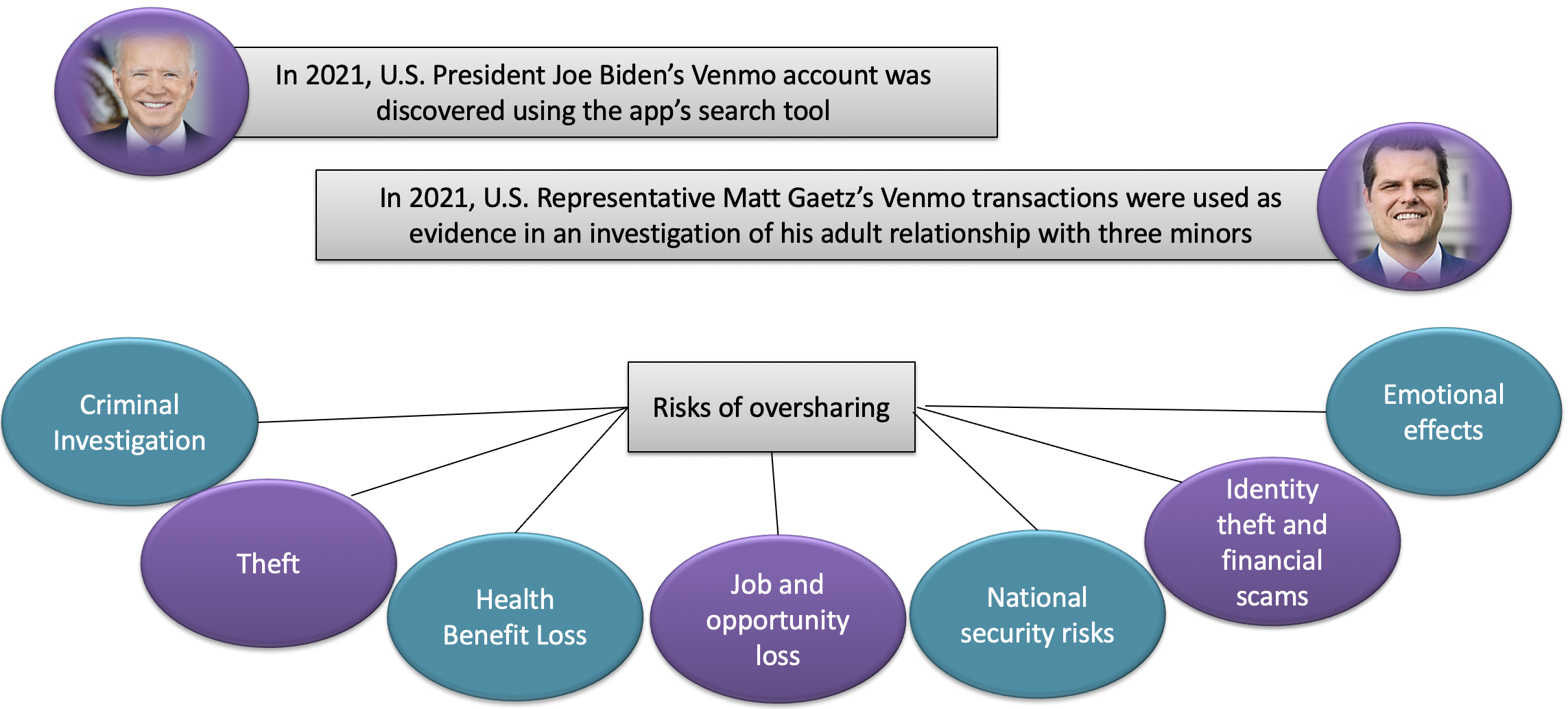
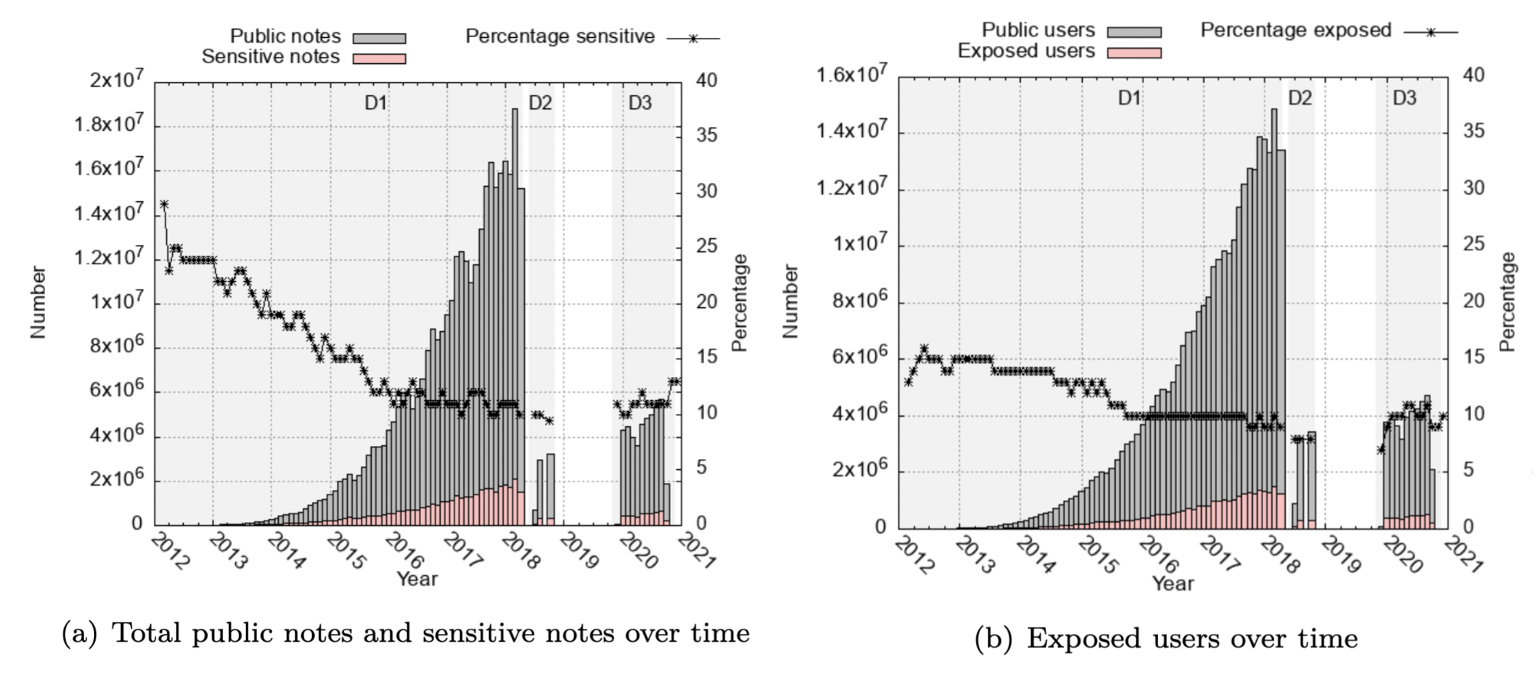
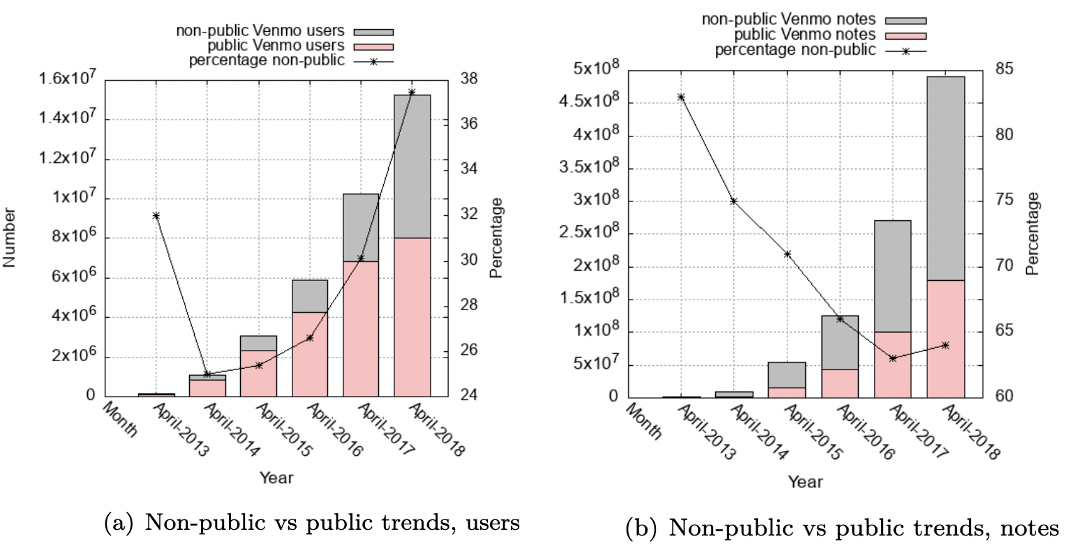
Venmo is a US-based mobile social payments platform. Each Venmo transaction requires a ``payment note'', a brief memo. By default, these memos are visible to all other Venmo users. Using three data sets of Venmo transactions, which span 8 years and a total of 389 M transactions with over 22.5M unique users, we quantify the extent of private data leaks from public transaction notes. To quantify the leaks, we develop a classification framework SENMO, that uses BERT and regular expressions to classify public transaction notes as sensitive or non-sensitive. We find that 41 M notes (10.5%) leak some sensitive information such as health condition, political orientation and drug/alcohol consumption involving 8.5 M (37.8%) users. We further find that users seek privacy by making their notes private, inconspicuous or cryptic. However, the large increase in Venmo's user base means that the number of users whose privacy is publicly exposed has grown substantially. Finally, the privacy of a user who transacts with a group on Venmo can be reduced or eliminated through the actions of other users. We find that this happens to around half of Alcoholics Anonymous, gambling and biker gang group members. Our findings strongly suggest that public-by-default payment information puts many users at risk of unintended privacy leaks.
Methodology
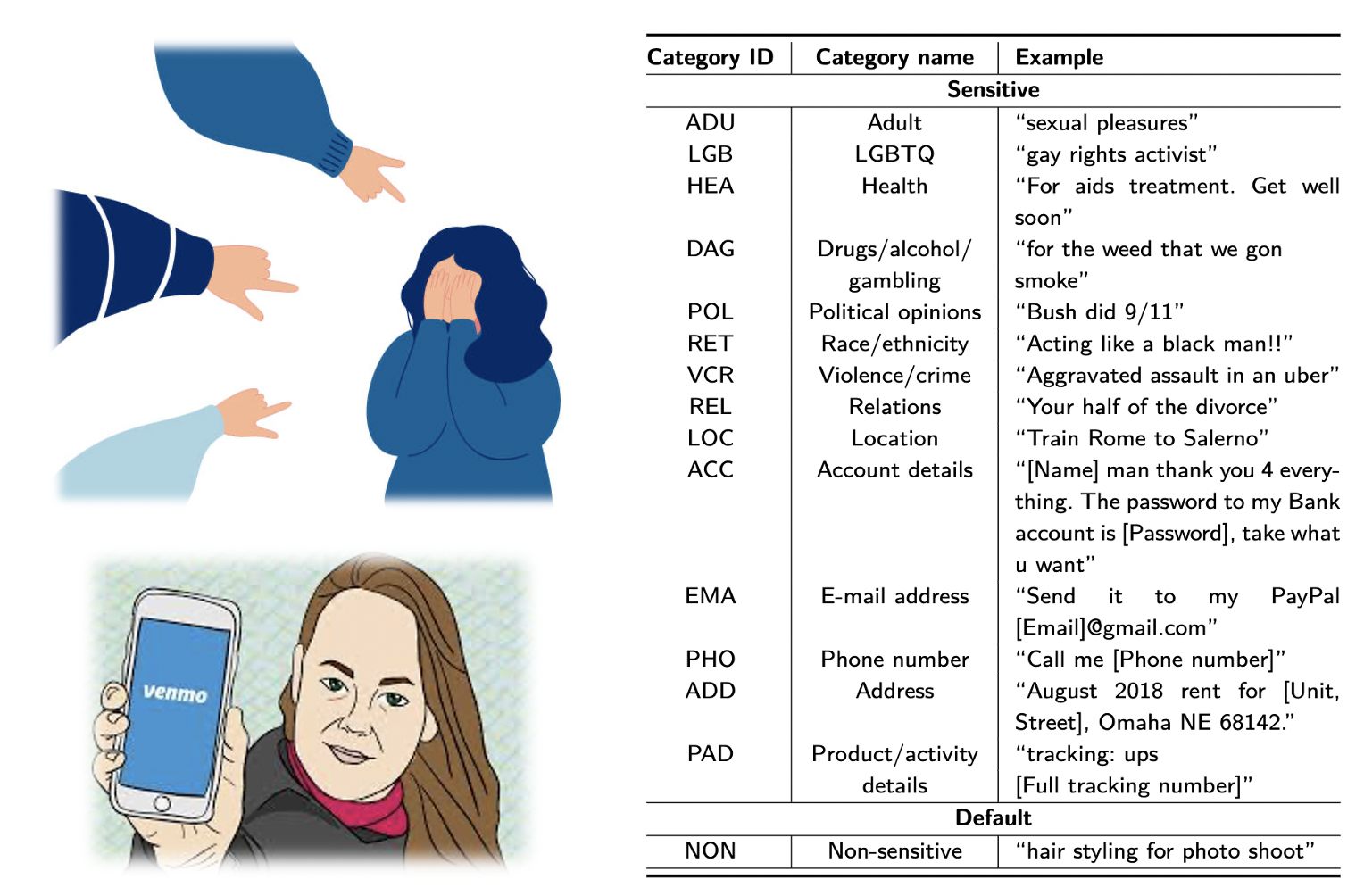
Identifying Sensitive Notes: Using BERT, we develop a classification framework, SENMO (SENsitive content on venMO). It classifies a transaction note as one or more of the sensitive categories. A note could also be classified as NON (non-sensitive), if it does not contain any sensitive information.
Measuring User Recourse: A user that does not know how to make their transactions non-public, may post cryptic notes. We define cryptic notes as notes that contain only emojis, only random numbers that do not match our regex patterns to infer sensitive content like phone numbers and addresses, only English interjections and greetings (e.g. “Hi”, “Hey”, “Aww”), only English stop words (e.g. “a”, “the”, “too”), use English letters, but do not contain a vowel, or are longer than 30 words.
Measuring Risks from Group Transactions: Membership in some groups may be considered sensitive – it may pose privacy risk to a user, if it is publicly known. We focus on three types of groups in this work: Alcoholics Anonymous, gambling and biker gang groups. We apply a keyword/activity heuristic to identify sensitive groups: identification of candidate sensitive groups, pruning of low-activity groups and pruning of unrelated groups.
Findings
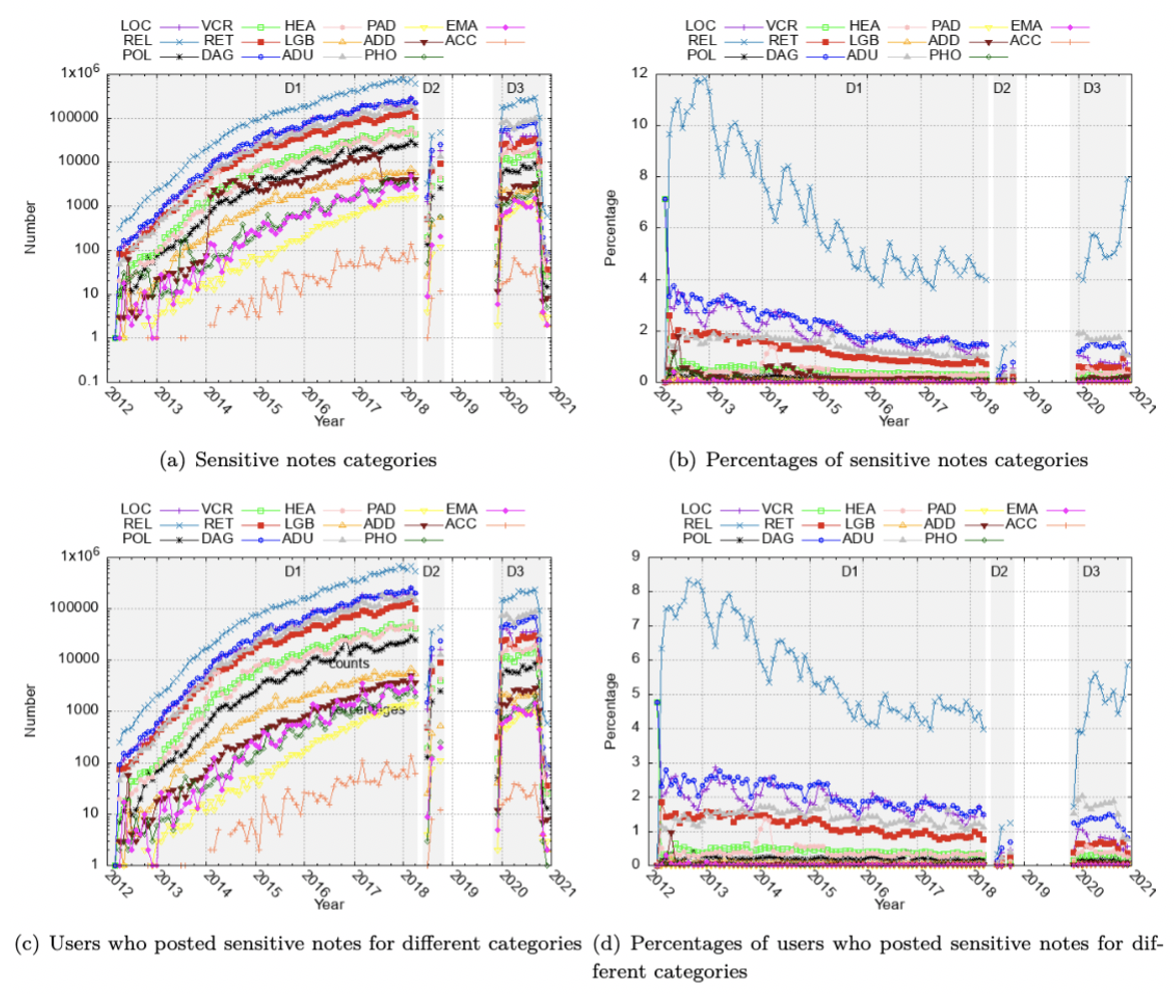
Privacy leakage affects many transaction notes and users: 41M notes out of 389M notes (10.5%) leak some sensitive information and 8.5M users out of at least 22.5M unique users (37.8%) are affected. REL and DAG are two of the most frequent categories. Privacy leakage increases over time, in spitef user measures to contain it. Among the group users that we found, around 40%–50% of users post at least one sensitive or common-pattern note, rest attempt to hide their membership by posting unrelated notes. However, all the users (503K users who posted a note in these groups) are affected.
News Articles and Discussions about our research
- The Guardian: ‘She’d been sending herself payments from me’: Venmo users on discovering secrets on the app
- USC: I know what you did on Venmo
- Eurekalert: I know what you did on Venmo
- FOX 5: Are your finances exposed? 2 in 5 Venmo users publicly reveal sensitive information
- MEL magazine: WE’RE ALL INADVERTENTLY SHARING OUR PERSONAL DATA AND CRIMES ON VENMO
- Western Slope Now: Are your finances exposed? 2 in 5 Venmo users publicly reveal sensitive information
- Reddit: I know what you did on Venmo: Discovering privacy leaks in mobile social payments
- ISI: I Know What You Did on Venmo
- Funancial News: We all unknowingly own personal data and crime Venmo. sharing on
- StudyFinds: Are your finances exposed? 2 in 5 Venmo users publicly reveal sensitive information
- Popular Mechanics: Don’t Take Privacy on Venmo for Granted
- WNN: 2 in 5 Venmo users publicly reveal sensitive information
- AP News: Are your finances exposed? 2 in 5 Venmo users publicly reveal sensitive information
- Reddit: I know what you did on Venmo: Discovering privacy leaks in mobile social payments
- WFXR FOX news: Are your finances exposed? 2 in 5 Venmo users publicly reveal sensitive information
- The local report: Are your finances exposed? 2 in 5 Venmo users publicly reveal sensitive information
- Planet Concerns: Are your finances exposed? 2 in 5 Venmo users publicly reveal sensitive information
- Techy Job: Are your funds uncovered 2 in 5 venmo customers publicly reveal delicate information
- Tampa Hoy: Are your finances exposed? 2 out of 5 Venmo users publicly disclose sensitive information
- Novonite: 2 in 5 Venmo Users Publicly Reveal Sensitive Information
- YRT News: Are your finances exposed? 2 in 5 Venmo users publicly reveal sensitive information
- Antiguaandbarbuda news: 2 in 5 Venmo users publicly reveal sensitive information
- Don't take privacy for granted on Venmo
- Eyelash news: Are your finances at risk? 2 out of 5 Venmo users disclose sensitive information publicly
- News10: 2 in 5 Venmo users publicly reveal sensitive information
- NP News Post: 2 in 5 Venmo users publicly reveal sensitive information
- KFOR-TV: 2 in 5 Venmo users publicly reveal sensitive information
- World Report: 2 in 5 Venmo users publicly reveal sensitive information
- Web News 24: 2 in 5 Venmo users publicly reveal sensitive information
- Crystal Gorham: Are your finances exposed? 2 in 5 Venmo users publicly reveal sensitive information
- Spot on Oklahoma: Are your finances exposed? 2 in 5 Venmo users publicly reveal sensitive information
- WJBF-TV: Are your finances exposed? 2 in 5 Venmo users publicly reveal sensitive information
- TRENDRADARS: Are your finances exposed? 2 in 5 Venmo users publicly reveal sensitive information
- WWLP-22News: Are your finances exposed? 2 in 5 Venmo users publicly reveal sensitive information
- WNCT : Are your finances exposed? 2 in 5 Venmo users publicly reveal sensitive information
- KTLA: Are your finances exposed? 2 in 5 Venmo users publicly reveal sensitive information
- USC Viterbi School of Engineering: Are your finances exposed? 2 in 5 Venmo users publicly reveal sensitive information
- Spot on Oklahoma: Are your finances exposed? 2 in 5 Venmo users publicly reveal sensitive information
- OZKARFIRST: Are your finances exposed? 2 in 5 Venmo users publicly reveal sensitive information
- WLNS: Are your finances exposed? 2 in 5 Venmo users publicly reveal sensitive information
- Top news USA: 2 in 5 Venmo users publicly reveal sensitive information
- MSN: Are your finances exposed? 2 in 5 Venmo users publicly reveal sensitive information
- Opera News: 2 in 5 Venmo users publicly reveal sensitive information
- WETM TV 18: 2 in 5 Venmo users publicly reveal sensitive information
- Yahoo: A New Study Reveals Lots of People Inadvertently Share Way Too Much Private Info on Venmo
- CW39: Are your finances exposed? 2 in 5 Venmo users publicly reveal sensitive information
- iCITI: Payment software Venmo may leak personal privacy information? !
- WJMN-TV: Are your finances exposed? 2 in 5 Venmo users publicly reveal sensitive information
- Inside Headline: Are Your Finances Exposed? 2 In 5 Venmo Users Publicly Reveal Sensitive Information
- 2 in 5 Venmo users publicly reveal sensitive information
- Planet Circulate: Are Your Finances Exposed? 2 In 5 Venmo Users Publicly Reveal Sensitive Information
- World get news: 2 in 5 Venmo users publicly reveal sensitive information
- The news progress: 2 in 5 Venmo users publicly reveal sensitive information
- 8 news: Are your finances exposed? 2 in 5 Venmo users publicly reveal sensitive information
- KARK News: Are your finances exposed? 2 in 5 Venmo users publicly reveal sensitive information