Members and Collaborators
Overview
Exploit-based denial-of-service attacks (exDoS) are challenging to detect and mitigate. Rather than flooding the network with excessive traffic, these attacks generate low rates of application requests that exploit some vulnerability and tie up a scarce key resource. It is impractical to design defenses for each variant of exDoS attacks separately. This approach does not scale, since new vulnerabilities can be discovered in existing applications, and new applications can be deployed with yet unknown vulnerabilities.
Our Solution
We propose Leader, an application-agnostic and attack-agnostic defense against exDoS attacks. Leader monitors fine-grained resource usage per application and per each external request to that application. Over time, Leader learns the time-based patterns of legitimate user's usage of resources for each application and models them using elliptic envelope. During attacks, Leader uses these models to identify application clients that use resources in an abnormal manner, and blocks them. We implement and evaluate Leader for Web server protection against exDoS attacks. Our results show that Leader correctly identifies over 99% of malicious IPs, and over 99\% of legitimate user IPs across the six different exDoS attacks used in our evaluation. On the average, Leader can identify and block an attacker after 6-7 requests. Leader has a minimal run time overhead, with an aggregate added latency below 0.5%.
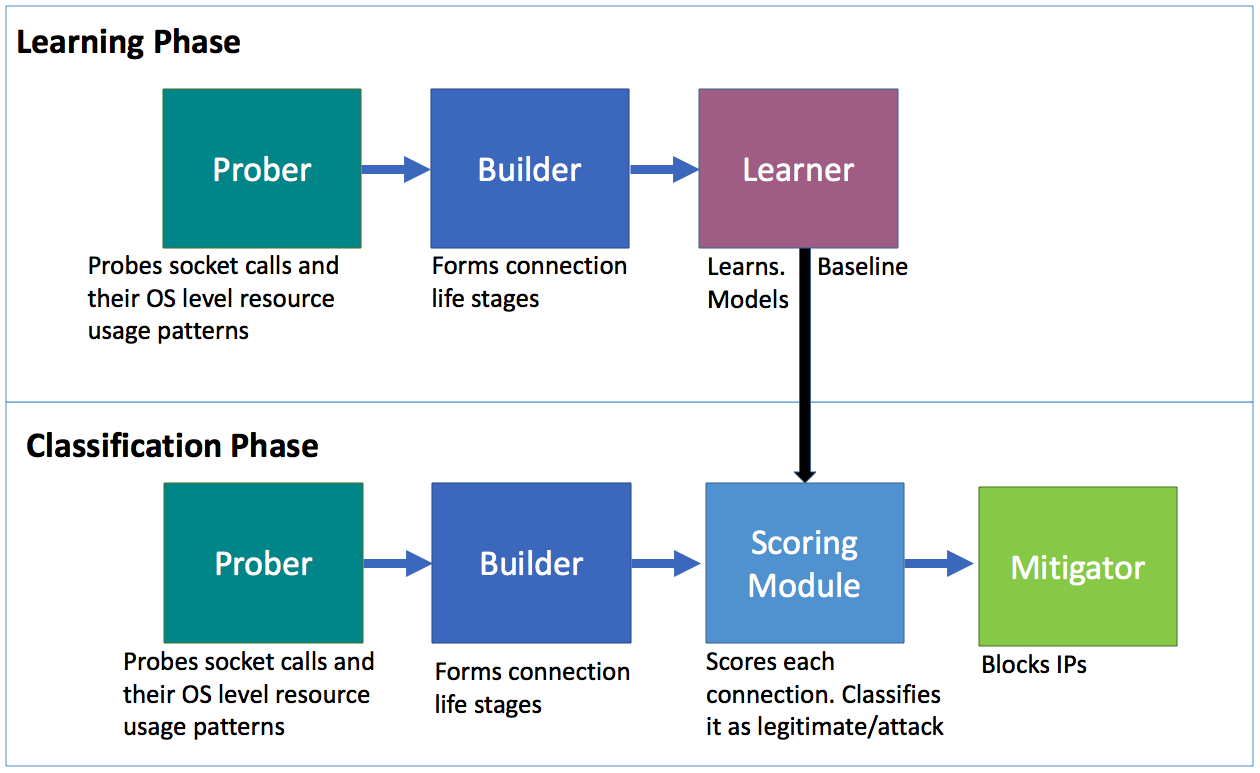
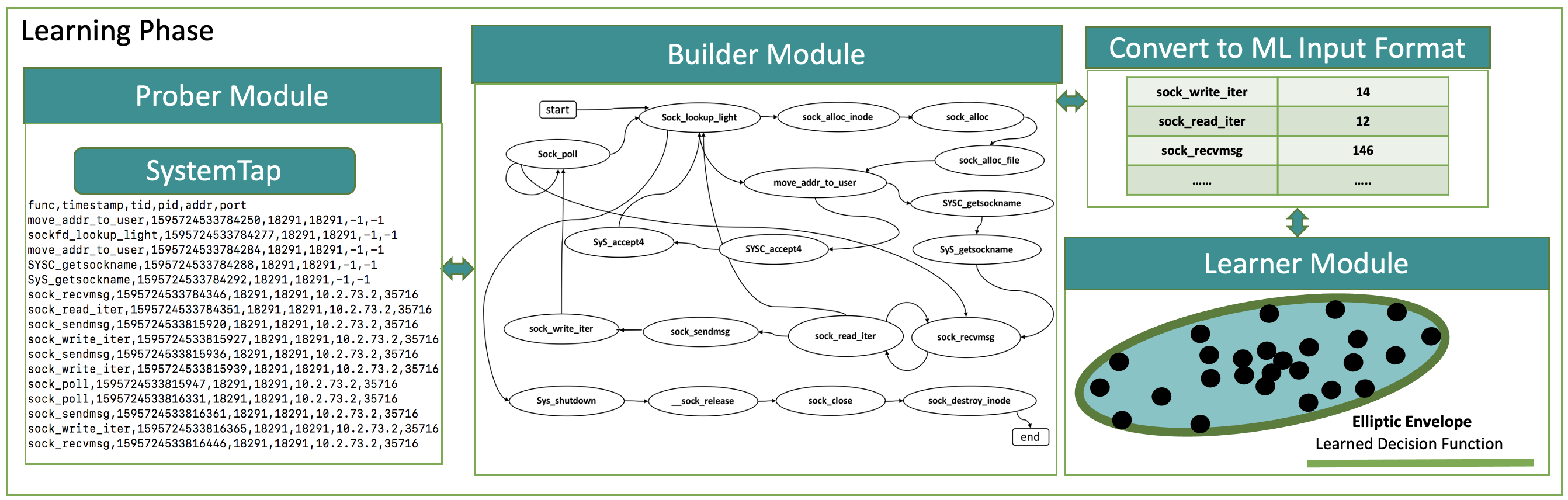
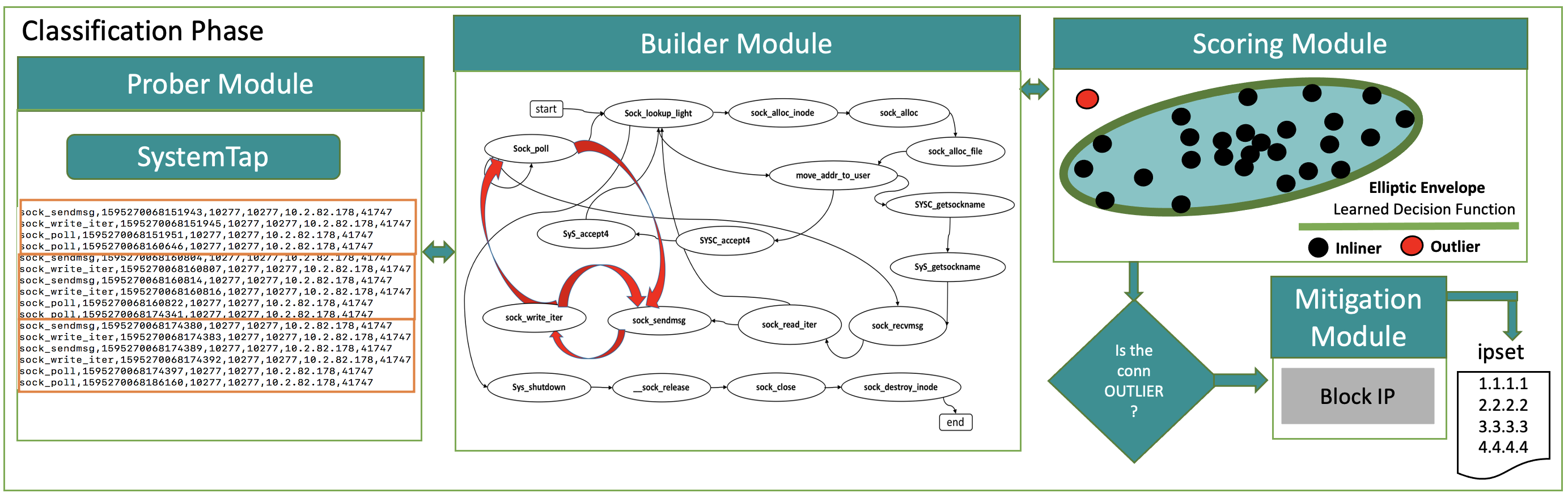
The main novelty of Leader lies in its approach to build models of resource usage for each incoming network connection. In order to do so, our new approach captures sequences of resource-use events -- which we dub connection life stages - in a temporal and relational manner for each incoming service request. Connection life stages are built from multiple, complementary observations collected at the (1) network level, (2) OS level and (3) application level. Connection life stages are then clustered into resource-use profiles for each application. Leader learns baseline profiles during no-attack periods, using a machine learning approach based on elliptic envelope. When an attack is detected, Leader uses its baseline profiles to detect anomalous resource-use patterns and links them back to the incoming responsible connections. Sources of these incoming connections are then blacklisted to mitigate the attack.
While our design of Leader is application-agnostic and attack-agnostic, in this paper we focus on building and evaluating Leader for the protection of Web servers against LDR attacks. We implement Leader using SystemTap to probe individual connections at socket function call level. For each function call to net/socket.c, Leader collects and maintains information about the connection, its temporal resource consumption, call sequences and call frequencies. Leader operates in two phases: the learning phase and the classification phase. During the learning phase it learns these resource usage patterns by legitimate users' connections, as a baseline model. During the classification phase, it terminates connections and blacklists clients whose connections consume resources in a way that deviates from Leader's models.
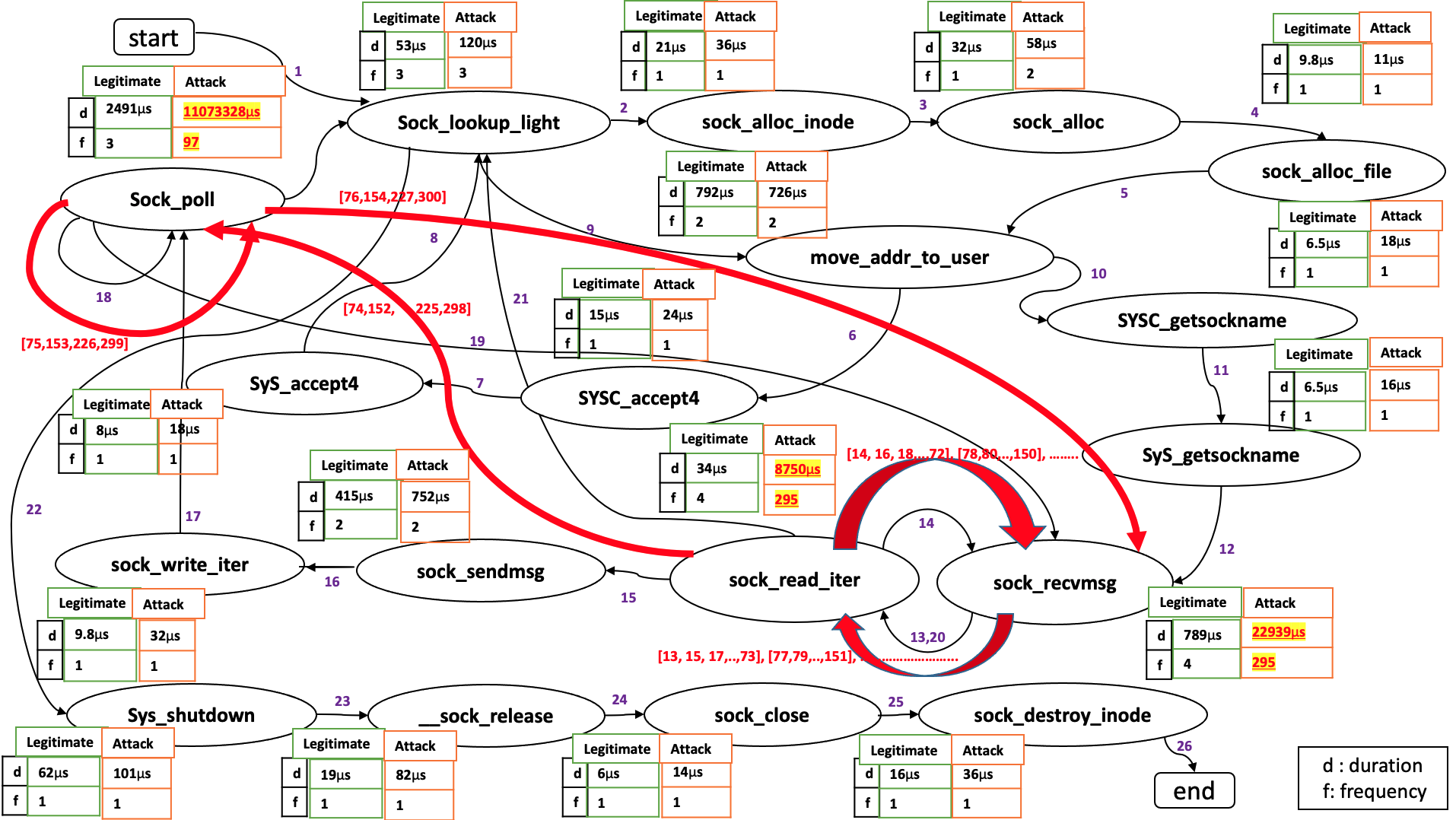
Sample legitimate and attack connection life stages. Numbers above the edges denote the order of transitions. The tables with each stage show theduration of the stage and how often it is visited in the sequence. The red portion shows the sequence of calls in an exDoS attack that are different from the callsobserved on a legitimate connection. Different exDoS attacks may follow different sequences and consume different amount of resources at different calls.
Results
We test Leader in emulated experiments on the Emulab testbed using two different Web servers. We mirrored Imgur and Wikipedia. Imgur runs on apache2, while we setup Wikipedia on nginx. We replay human user traffic collected using Amazon MTurk workers. We evaluate Leader using on different exDoS variants: Slowloris attack (SL), Hash Collision Attack (HC), Regular Expression Denial of Service Attack (ReDoS), exDoS using preg_replace() PHP Function Exploitation (PHPEx), Security Vulnerability - Infinite recursive calls denial of service (IRC) and Maliciously Crafted URL Attack on a Flask Application (MCU).
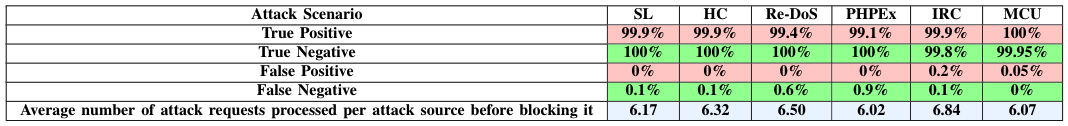
Our results show that, in the liberal scenario, Leader is capable of handling many variants of exDoS attacks, while being trained only with legitimate traffic. In our evaluation Leader achieved the aggregate accuracy of over 99% in identifying the attacker IP addresses and an aggregate accuracy of over 97.5% in identifying the legitimate user IP addresses across the five different exDoS attacks. On the average, Leader can successfully identify and blacklist a stealthy attacker in 5 to 18 seconds and an aggressive attacker in 4 to 12 seconds. Leader has a minimal run time overhead with an aggregate latency of less than 0.5%.

Conservative design requires that a connection receives some portion of anomalous classifications before it is regarded as an attack. This approach should reduce misclassification of legitimate connections, at the expense of longer decision time. Here, Leader achieves higher than 99% accuracy for both legitimate and attack source identification, but it takes 6–7 requests per source for classification.